Spreading Malware and Compromising Systems
The first of these phishing mails were reported by IBM X-Force and twitter user bom.
Specifically targeting Japanese citizens, these emails were sent by a very dangerous threat group referred to as “TA542”.The emails contained payloads of the Emotet malware. This payload was hidden in this case primarily in Microsoft Word Documents.
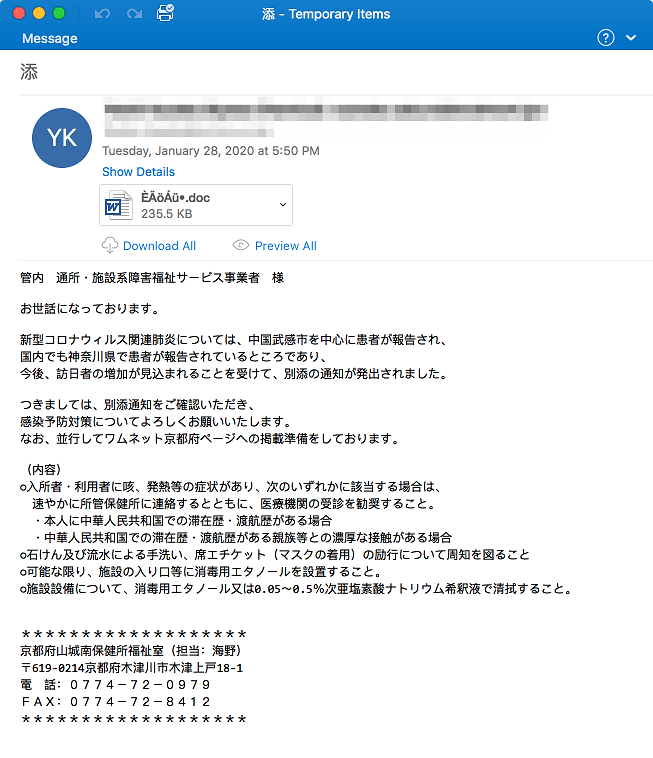
The above email is roughly translated as:
Jurisdiction tsusho / facility related disability welfare service provider.
We become indebted to.
Patients were reported about the new type of coronavirus- related pneumonia, mainly in Takeshi, China.
Patients have been reported in Tottori Prefecture in Japan,
Therefore, please check the attached notice,
Thank you for your infection prevention measures.
In parallel, we are preparing to publish on the Wamnet Kyoto page
The main aim of this email was to lure the victim into downloading a Microsoft Word file and enabling macros. After which an Emotet downloader is installed discreetly on to the victim’s computer. Compromising the victim’s system entirely. Emotet has always shown a tendency to use the latest news and the going on in the world to spread their malware. Previously using Greta Thurnberg and Halloween as attack vectors.
Another similar case of malware being dropped through this email was found by the mimecast security team.
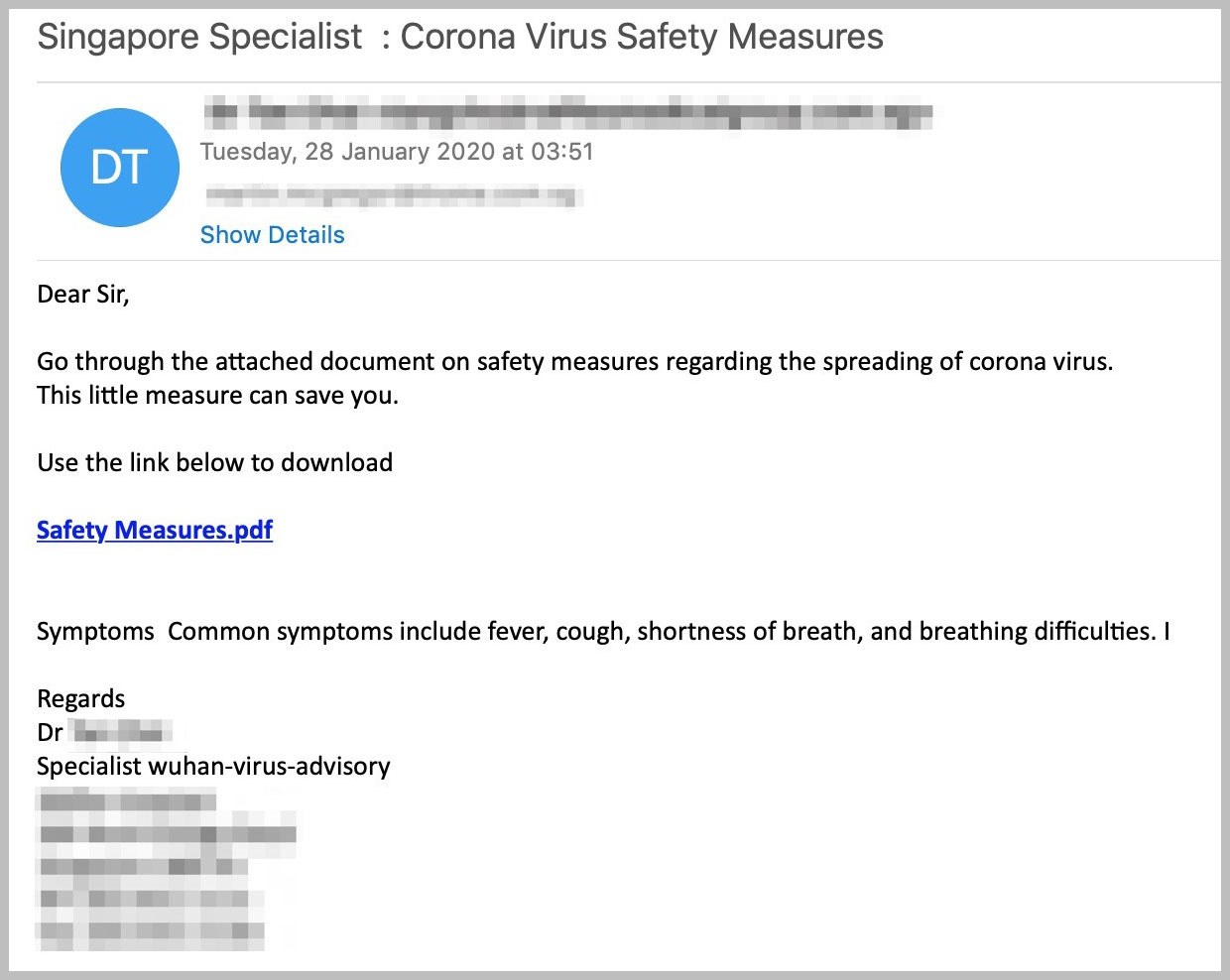
Here the Doc file is replaced by a poisoned PDF, opening which would lead the user to a malicious link, which would prompt the user into downloading a virus filled document
Stealing Credentials
The next type of attack is the classic credential stealer, here the attacker redirects you to a malicious phishing page of a legitimate website and asks for your login details or other sensitive information. Found by the KnowBe4 team ,the below email redirects the victim to a fake Outlook-Themed phishing page, where the credentials of the user can be compromised.
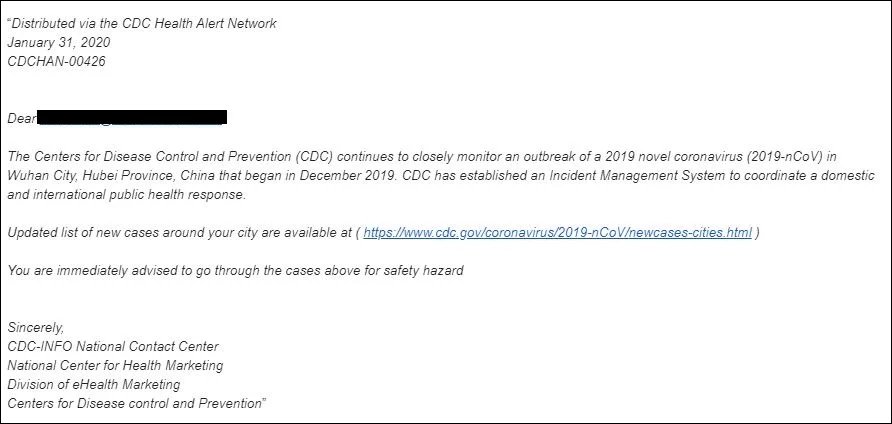
Another instance involves the attackers using the World Health Organization’s website and information to trick the victim.

Despite the bad English and grammatical mistakes, the presence of the WHO logo and the “From” address, lend this email credence. If the link is clicked the following page pops up.
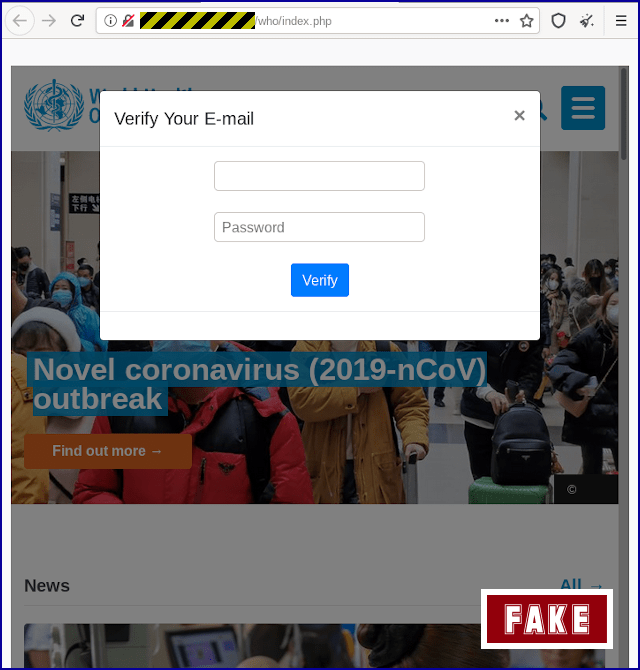
The form if filled, sends those details straight to the attackers, while the victim is redirected to WHO home page. Leaving no signs of tampering. The latest in these cases was reported by MalwareBytes, here an email was discovered that asked for donations to help in the creation of a vaccine. The link embedded in the email redirected to another phishing page, where the victims credentials could be stolen.
Possible Threats
Also the latest reports suggest that WeChat, the Chinese competitor to WhatsApp and iMessage, has also risen as a vector for these attacks, according to Chinese officials. If this turns out to be the case, do not be surprised if messaging applications such as WhatsApp also become an avenue used by these attackers.
If you think that you have received such an email or malicious message, please reach out to us at Report a Case , and remember to always exercise caution when dealing with any email or message that may seem suspicious.