An In-Depth Analysis of How an OLX Scam Works
Garmin services specifically their Connect App, their aviation focused apps and products were down from 24th July to 27 July. This outage also affected all their call centers, emails and support rooms.
The attack started on Wednesday, 23 July, with multiple users being unable to sync and use the Garmin Connect app on their phones.
Reports on Wednesday also suggested outages and problems with the Garmin suite of marine, aviation and navigation services. The Garmin Pilot app, which allows pilots to copy flight plan databases, had been rendered unusable.
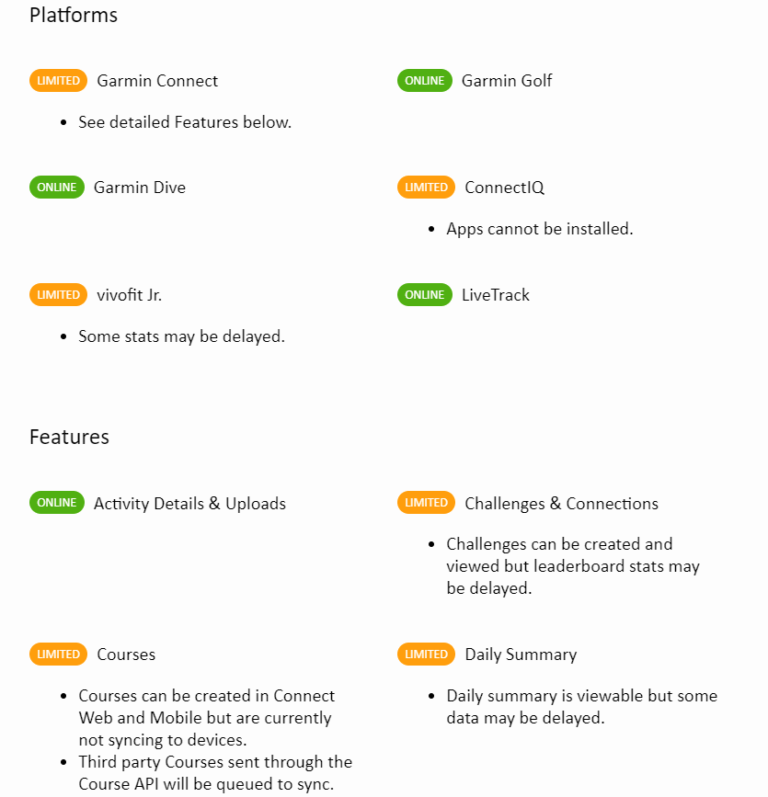
At the time this article was written, Garmin have been able to restore their apps and services with limited functionalities. As listed out on the Garmin website:
As all these app outages continued to be reported by the users, Garmin issued a statement on their Twitter account.
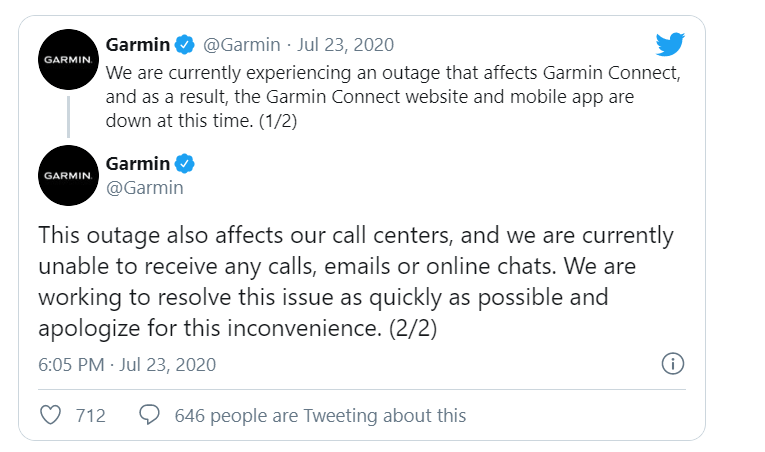
The outage had spread to affect all Garmin call centers, and almost every mode of direct communication to Garmin had been compromised. All emails sent to any Garmin email address from the 23rd of July to the 27th of July failed to reach their destination. But as the last year has shown, sufficiently skilled attackers can compromise physical systems and operation of companies as well. According to reports from a local news outlet in Taiwan, Garmin’s prediction lines were completely stopped for two days, the 24th and 25th. This was according to an internal email that was leaked to the public.
The WastedLocker Ransomware
As the attack continued and Garmin services still weren’t up, several security researchers and companies looked to find the attack that had targeted Garmin.
Due to some excellent work from the researchers at BleepingComputer, the exact attack was found out to be a Ransomware attack, specifically using the Wasted Locker Ransomware. They researchers were able to retrieve photos of the actual encrypted files on a Garmin system.
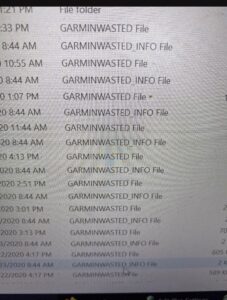
They were also able to get their hands on the ransom note that was created during the attack.
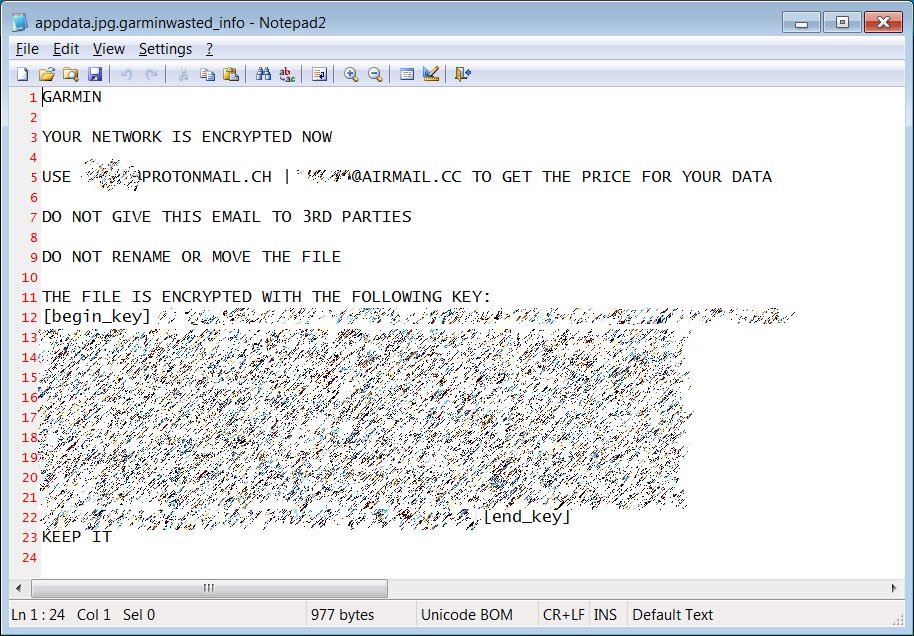
This ransom note is very similar to the ones received by previous WastedLocker victims. Due to the relative recency and obscurity of the WastedLocker ransomware there hasn’t been any decryption tool made for it yet. All decryption tools created for ransomwares are listed out on NoMoreRansom.org.